Five Areas Where Hotels Are Prone to Attack:
1. Point–of–Sale
Point–of-sale (POS) attacks have historically been the number one cause for concern among hoteliers and pose an enormous threat to the hospitality industry. These kinds of attacks use malware to target third party vendors by exploiting weaknesses in the hotel’s system. When cybercriminals discover this error, they can steal credit card data from millions of guests.
POS malware usually targets systems that handle credit card data, and by using techniques such as memory scraping/dumping and keystroke-logging functionality, they can capture large quantities of card data.
Web applications and mobile applications used in POS transactions are easily accessed by hackers, making them a huge target. Breaches are especially prevalent in hotels who don’t have security plans and best practices firmly established. It’s also important to hire employees with a strong technical background to keep you apprised of security and technology trends.
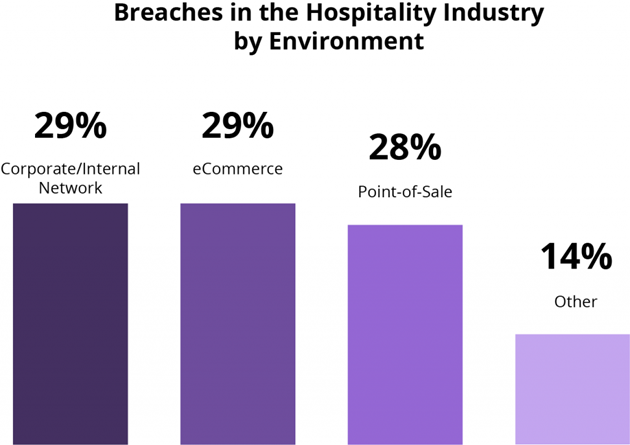
- POS systems comprised 28% of breaches.
- 60% of these were phishing scams.
- 43% targeted card track data.
2. Corporate/Internal Networks
Another common method cybercriminals use to gain access to guests’ information is the hotel’s WiFi network. Hotel guests are particularly vulnerable to hackers when they utilize the hotel’s WiFi. Logging on to an open network immediately puts them at risk for getting hacked, and once a device is breached, hackers can install spyware to view all their activity. This includes any financial information they may have on their device. This data can then be used as part of a phishing campaign against the individual.
In addition to an open WiFi network, hackers can also create their own WIFI networks in order to trick guests. A traveler can easily fall victim to this scam and login to a false network without ever realizing it.
Cybercriminals can also upload malicious malware to a hotel’s server enabling them to target specific guests and trick them into downloading infected software. In recent years, these types of attacks have become more advanced and usually target those in a position of authority, taking over their email and sending fake emails to colleagues. These attacks generally seek a financial gain.
As a precaution, you should implement separate WiFi networks for social and professional use.
- Corporate and internal networks made up 29% of attacks.
- 45% of all inbound emails contained spam.
3. eCommerce
eCommerce is a huge target for cybercriminals due to the large volume of credit card data and personal information being entered, and stored, on hotels’ websites. Any web server that’s used for processing payment information or personally identifiable information (PII) is at risk for attack.
Criminals have certain tools and techniques at their disposal to infiltrate sites that deal with eCommerce transactions. Using malicious scripts, they’re able to skim and capture payment information from unaware guests.
Web applications serve as a powerful tool to connect consumers with services, allowing for more transactions to be completed online than in-person. In turn, this makes them a target for attackers who are looking for a way to steal credit card information. Once card data has been stolen, it’s highly likely that it will be sold on a dark web marketplace and used by criminals on other eCommerce sites.
It’s important to pay attention to where your specific vulnerabilities are and how you can work to mitigate the threat.
- eCommerce made up 29% of attacks.
- 25% of incidents targeted card-not-present (CNP) data.
- 32% of targeted financial information or user credentials.
4. Physical Attacks
Keep in mind that not all security threats are cyber related. You should never underestimate what a criminal can do in person if you let your guard down.
Physical security breaches can be the most simple and straightforward method of attack, but often overlooked. Just by being in the vicinity of a hotel, criminals can easily access a hotel’s servers, computers, and terminals.
One of the easiest things you can do is train your employees on what to look out for in terms of suspicious behavior. Engaging guests during check-in also goes a long way in not only creating a welcoming atmosphere, but also in determining who might be a potential threat. If you notice someone exhibiting behaviors that are different than your typical guest, you may want to pay more attention to their actions.
You can also install video surveillance systems to keep an eye on the things that your employees can’t.
- 25% of hospitality companies don’t provide any security training.
- 18% of hospitality companies only train their employees once during their employment.
- 31% of hotels don’t have a policy in place for storing and disposing confidential information.
5. Data Sharing Between Interconnected Systems
The world is getting smaller thanks to the ability to share information instantaneously, and your guests expect hotels to have accessible WiFi networks, mobile apps, and other hi-tech systems during their stay.
Hotels are also feeling the pressure to share their data between organizations such as travel management companies in order to make processes easier.
While this makes doing business exceptionally more efficient, it also makes hotels even more vulnerable to breaches. Each piece of technology a hotel uses increases their risk of a breach.
Even tools designed to protect you can be turned into a weapon. Hackers can target a wide variety of common devices and everyday systems. Things as simple as security cameras are vulnerable to attack. If these are breached, it can cause a chain reaction and bring down entire computer systems.
Having a firewall in place is critical in keeping your systems protected from attack.
- 67% of hotels’ websites leaked booking codes to third-party partners.
- 29% of sites sent emails containing unencrypted confirmation links, meaning hackers could intercept the data.
Smart Hotels: A New Trend
Everything is digital now, and some “smart hotels” have started integrating advanced features to enhance the guest experience. In many cases, guests never even have to interact with an individual during the whole check–in process. They’ll simply receive a text when their room is ready and can even unlock the door with their mobile phone.
But be aware, smart phone key cards present a real risk for guests. According to Reader’s Digest, smart keys can be intercepted from up to 15 feet away. This technology has yet to be perfected and is being exploited more and more frequently. You can be hacked anywhere at any time, so you must remain alert.
This kind of breach is also worrisome because it enables a criminal to gain direct access to a victim’s hotel room. It becomes just as much a physical safety concern as a cyber safety concern.
Additionally, many hotels are now starting to implement voice-controlled systems into their hotel rooms. Guests can utilize a voice-controlled assistant that does everything from ordering room service to turning on the TV. While many things about this are great, it comes with downsides as well.
By nature, interconnected devices are generally more vulnerable to security breaches on a larger scale. And with a voice-controlled system, you run the risk of people listening in, something Amazon recently admitted to with its employees, and all-around easier access to personal information.
Unfortunately, with every advance in technology comes a new way for criminals to infiltrate your security systems. The hotels who are embracing new and innovative technology are also the ones who are at higher risk. And yet, guests demand this kind of tech savvy experience during their visit.
Each aspect of your business needs to be carefully monitored and you need to have a technology team to keep you apprised of security trends and help you stay ahead of the criminals. Remember, don’t implement technology for the sake of technology without being aware of the potential risks associated with it.
At the end of the day, the most important thing is to be aware of your surroundings, monitor what points of entry criminals can access within your hotel, and devise security plans for how to prevent attacks, as well as for what to do in case of a breach.